Uncovering and Defeating Microarchitecture Attacks in Modern Processors
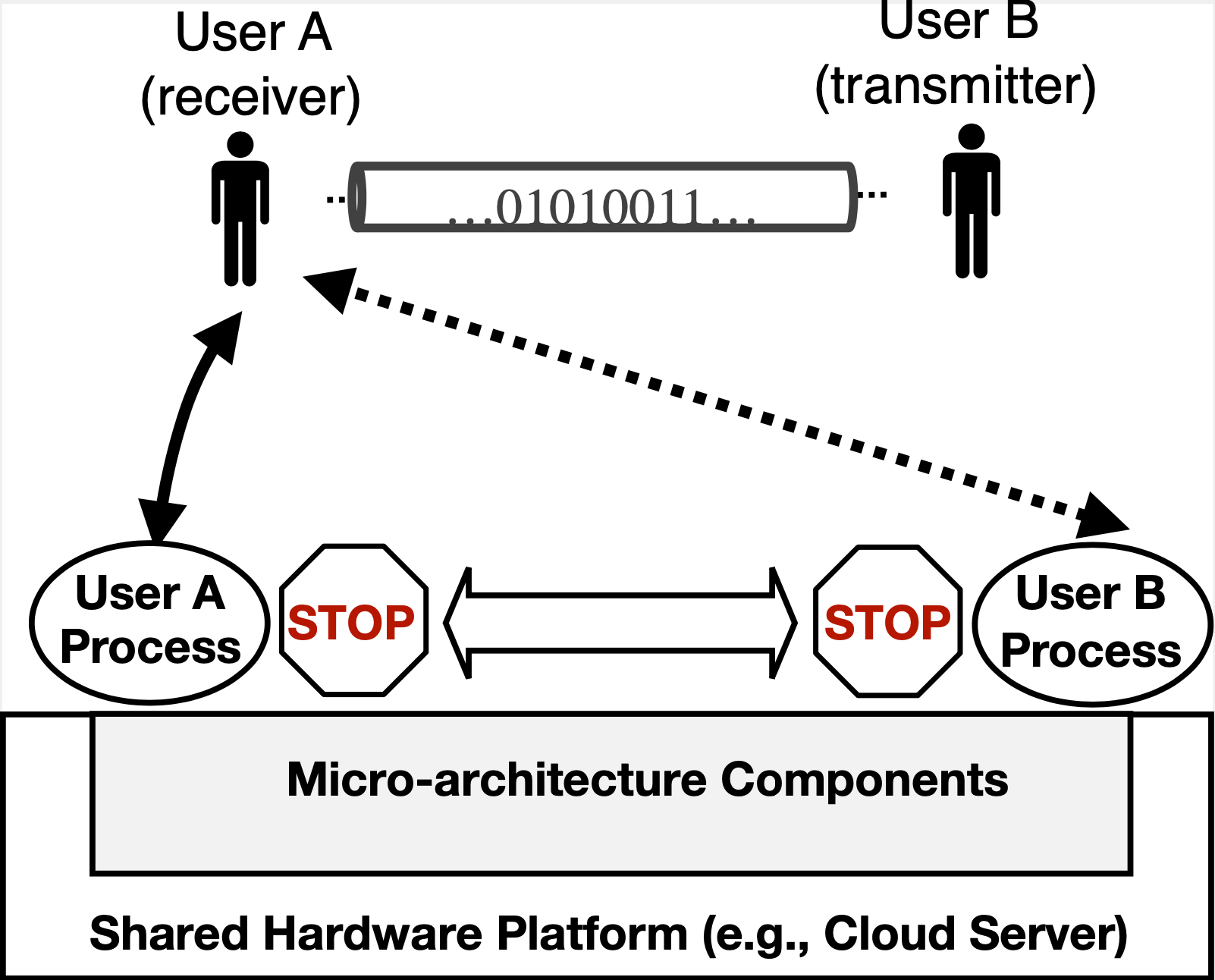
Safeguarding sensitive information stored in computing systems is a fast-growing concern as computers are ubiquitously used everywhere. Different from traditional software-level attacks, recent adversarial developments in side channels (e.g., Spectre and Meltdown) have demonstrated the practicality of exfiltrating sensitive data through directly exploiting security vulnerabilities in hardware. These attacks are extremely dangerous since they can bypass existing software-based protections and affect billions of commodity machines. Among the several forms of information leakage, timing channels manifest by exploiting the access timings of shared hardware resources that are not designed or even intended for communication. Such attacks are expected to be especially devastating in the cloud computing infrastructure as they allow adversarial users to break the underlying security primitives.
In this project, we will comprehensively investigate the information leakage attack surface in the microarchitecture design of modern processors with the goal of systematically uncovering new and unknown side channel attack vectors (both active and passive). We will identify the key causes of the unveiled side channel exploit and design low-cost and effective architectural and system-level defensive mechanisms to defeat these attacks.
